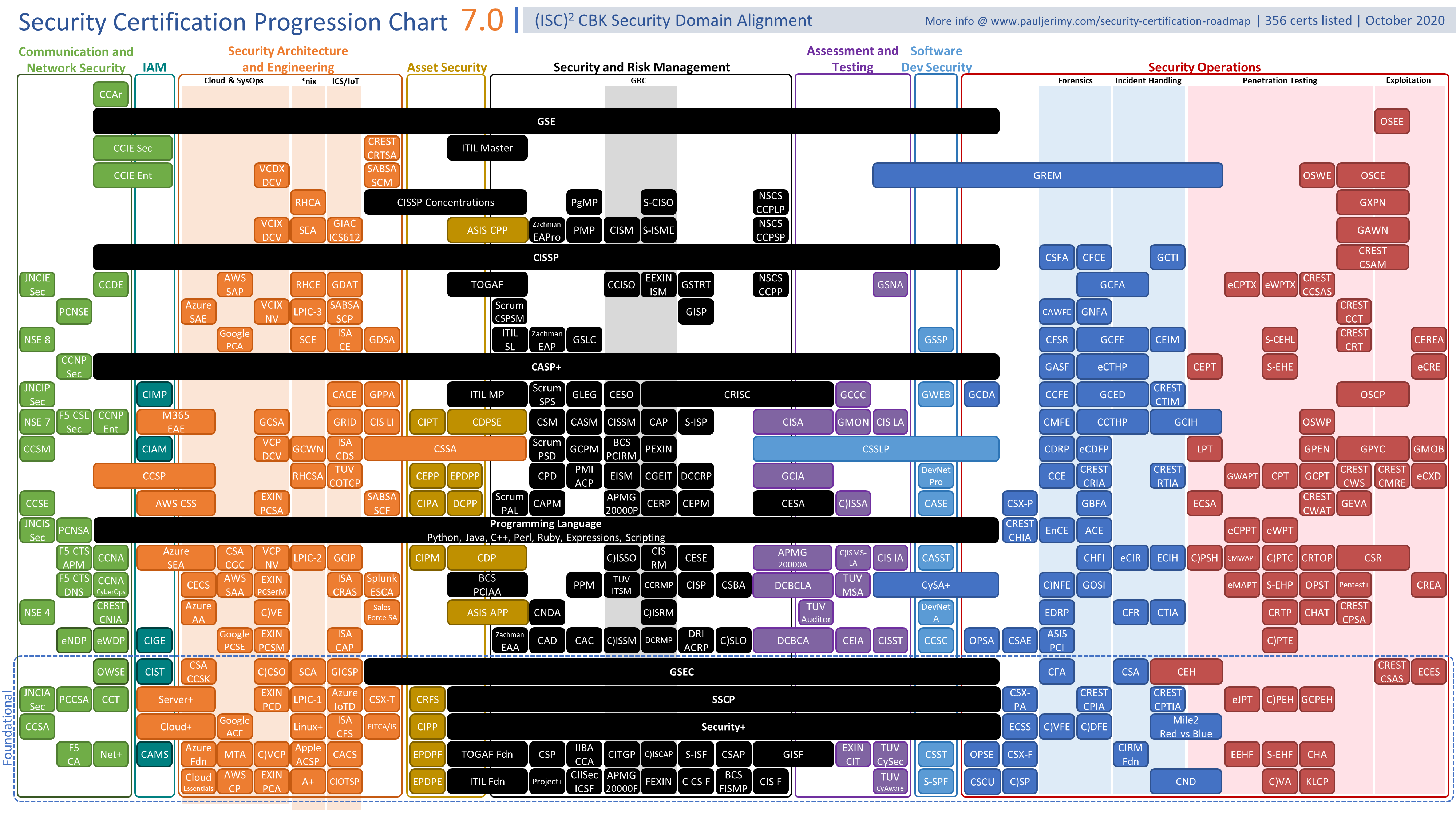
Security Certification Roadmap October 2020 Update
Feature Updates
This year has seen a big rise in popularity of the Security Certification Roadmap. In order to keep the information on there as useful as possible, I have made the following changes:
- Aligned the columns with (ISC)2 CBK security domains
- Moved certifications to new domains as applicable
- Adjusted some certification rankings in response to feedback
- Added 26 certifications
- Added Microsoft Edge support
- Updated scaling of the chart to full-width
- Added CSS to allow certifications to be cross domain
- Added the ability to have sub-domains
- Simplified the code to allow for easier updates
- Updated tooltip functionality to avoid off-screen clipping
Future Plans
The following features are in the works for this year:
- Links to more info on all 39 certificate issuing vendors represented in the roadmap
- Add a dark mode
- Reintroduce visual rows to indicate Beginner, Associate, Journeyman, or Expert levels
- Improve tooltip to include more information and be easier to read
The follow features are planned for the future when I learn how to implement them:
- Javascript version of the roadmap
- Add form options to re-order chart based on input such as:
- Highlight certifications from a specific vendor
- Highlight certifications that are user goals
- Highlight recommended certifications based on current achievements such as education, certifications, and experience
- Reorder roadmap based on career paths
- Reorder roadmap to exclude certifications for which the user has no interest
- Add certification planning tools such as saving customized charts, tracking milestones, linking to study resources, and comparing to template charts or other customized charts.
Request for Feedback
This roadmap has been 7 years in the making and community input has been the major driving force. In that spirit I want to encourage feedback for any aspect of the chart form formatting to ranking. Please use the form below if you want to contribute directly!

