Career Tools
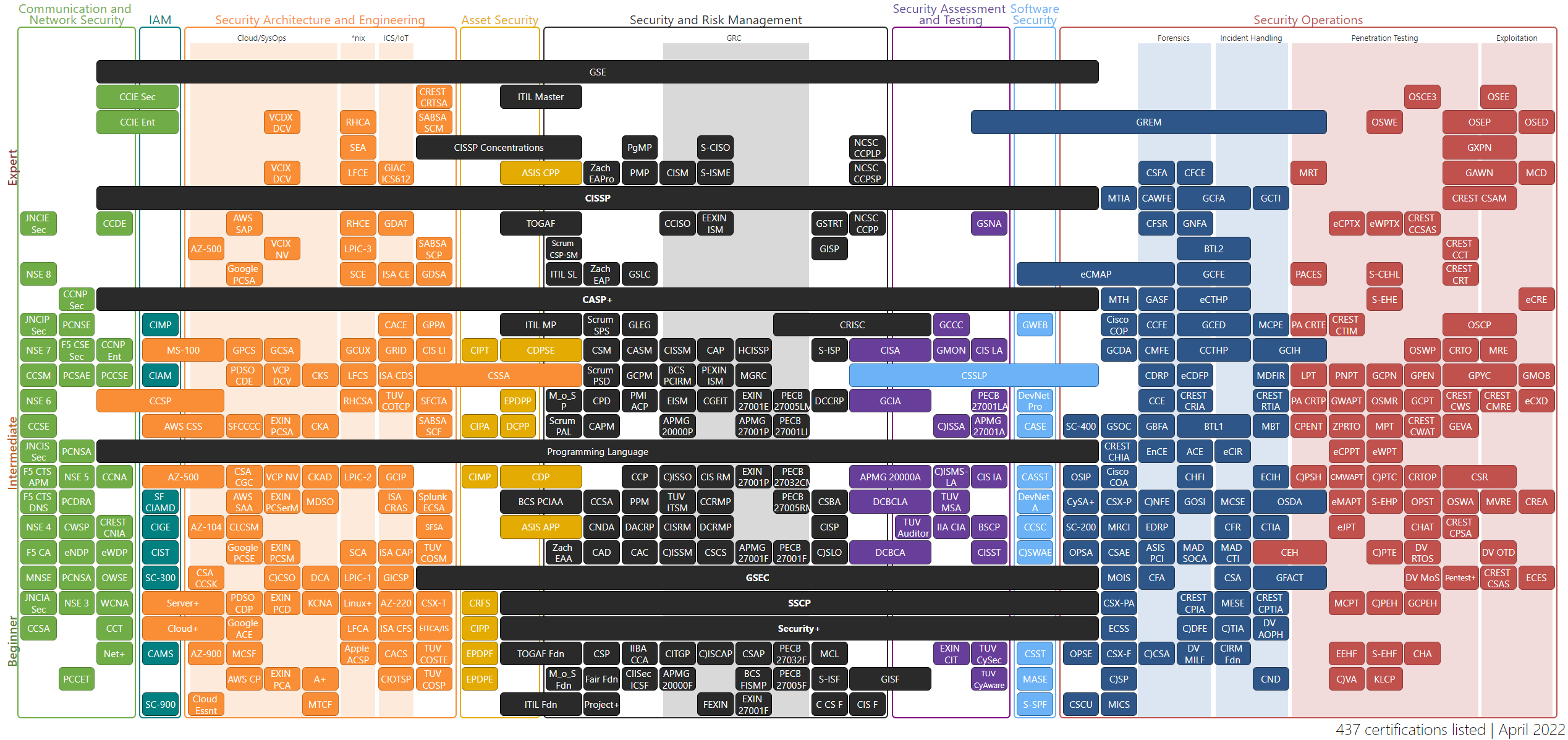
Security Cert Chart
460 IT security certifications arranged on a chart with basic information and links to each certification’s website.
Plan your continuing education path and browse other security domains.
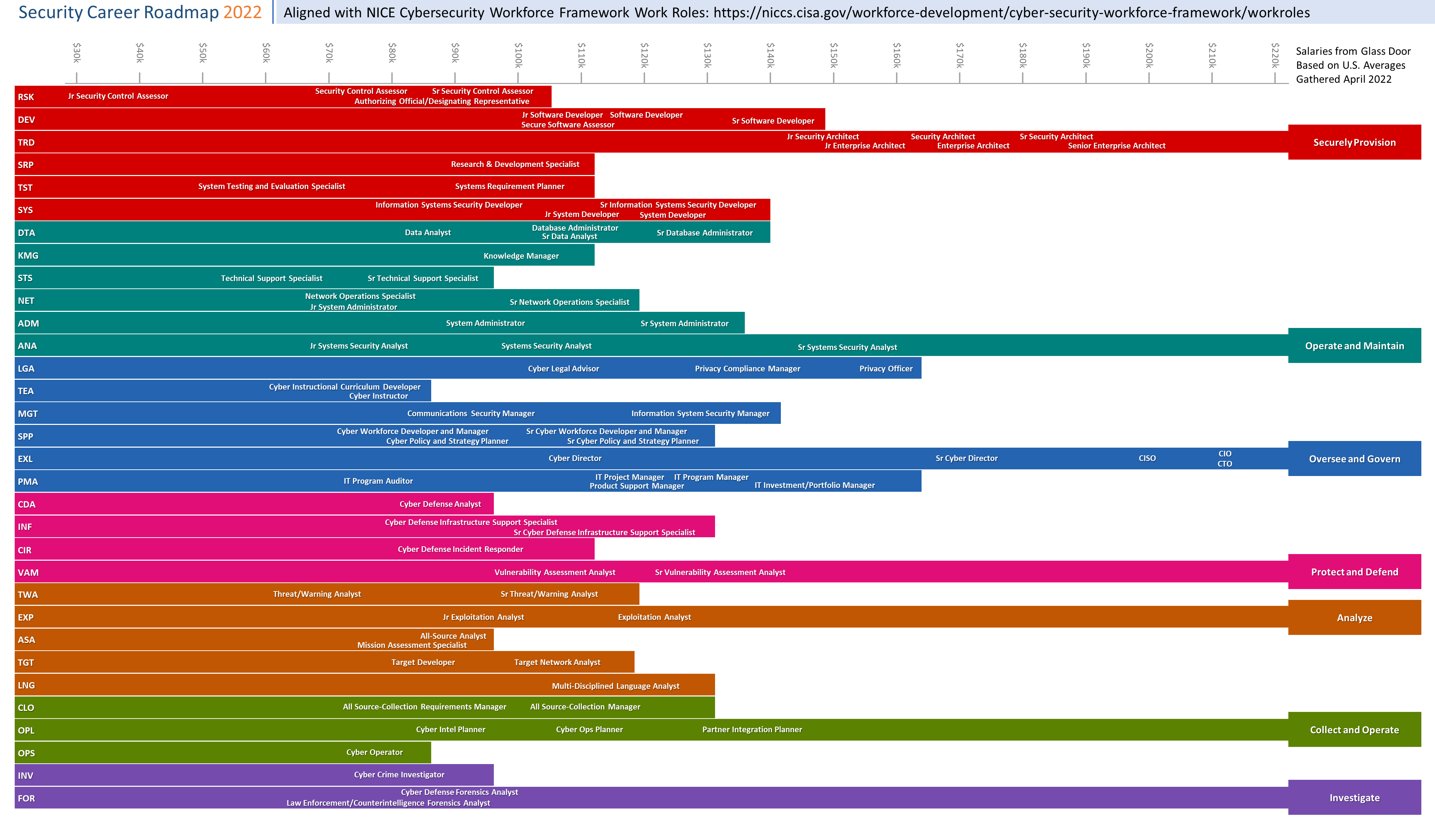
IT Career Roadmap
A chart of security work roles grouped NICE Framework specialty areas. See what positions typically make and plan your next step.
Most Recent Cyber Book Reviews
The Fifth Domain: A Solid Modern History for 2021
Summary The Fifth Domain: Defending Our Country, Our Companies, and Ourselves in the Age of Cyber Threats by Richard A. Clarke and Robert K. Knacke is a follow up to their 2010 novel Cyber War: The Next Threat to National Security and What to Do about It. This novel...
Rise of the Locusts: Cyber Bait and Switch
Synopsis Rise of the Locusts by Mark Goodwin is the first novel in his Cyber Armageddon series. The series follows a SOC Supervisor at a financial institute from the discovery of a breach through to the shutdown of critical infrastructure in the United States. The...
The Gam3: LitRPG with a little hacking
Synopsis The Gam3 is a 3 book series by the young author Cosimo Yap. The series follows the literary RPG style which blends the conventions of role-playing video games with a science fiction novel. In this style, the main protagonist is interacting with an RPG game...
The Latest

The Fifth Domain: A Solid Modern History for 2021
Summary The Fifth Domain: Defending Our Country, Our Companies, and Ourselves in the Age of Cyber Threats by Richard A. Clarke and Robert K. Knacke is a follow up to their 2010 novel Cyber War: The Next Threat to National Security and What to Do about It. This novel...
The Fifth Domain: A Solid Modern History for 2021
Summary The Fifth Domain: Defending Our Country, Our Companies, and Ourselves in the Age of Cyber Threats by Richard A. Clarke and Robert K. Knacke is a follow up to their 2010 novel Cyber War: The Next Threat to National Security and What to Do about It. This novel...
Rise of the Locusts: Cyber Bait and Switch
Synopsis Rise of the Locusts by Mark Goodwin is the first novel in his Cyber Armageddon series. The series follows a SOC Supervisor at a financial institute from the discovery of a breach through to the shutdown of critical infrastructure in the United States. The...