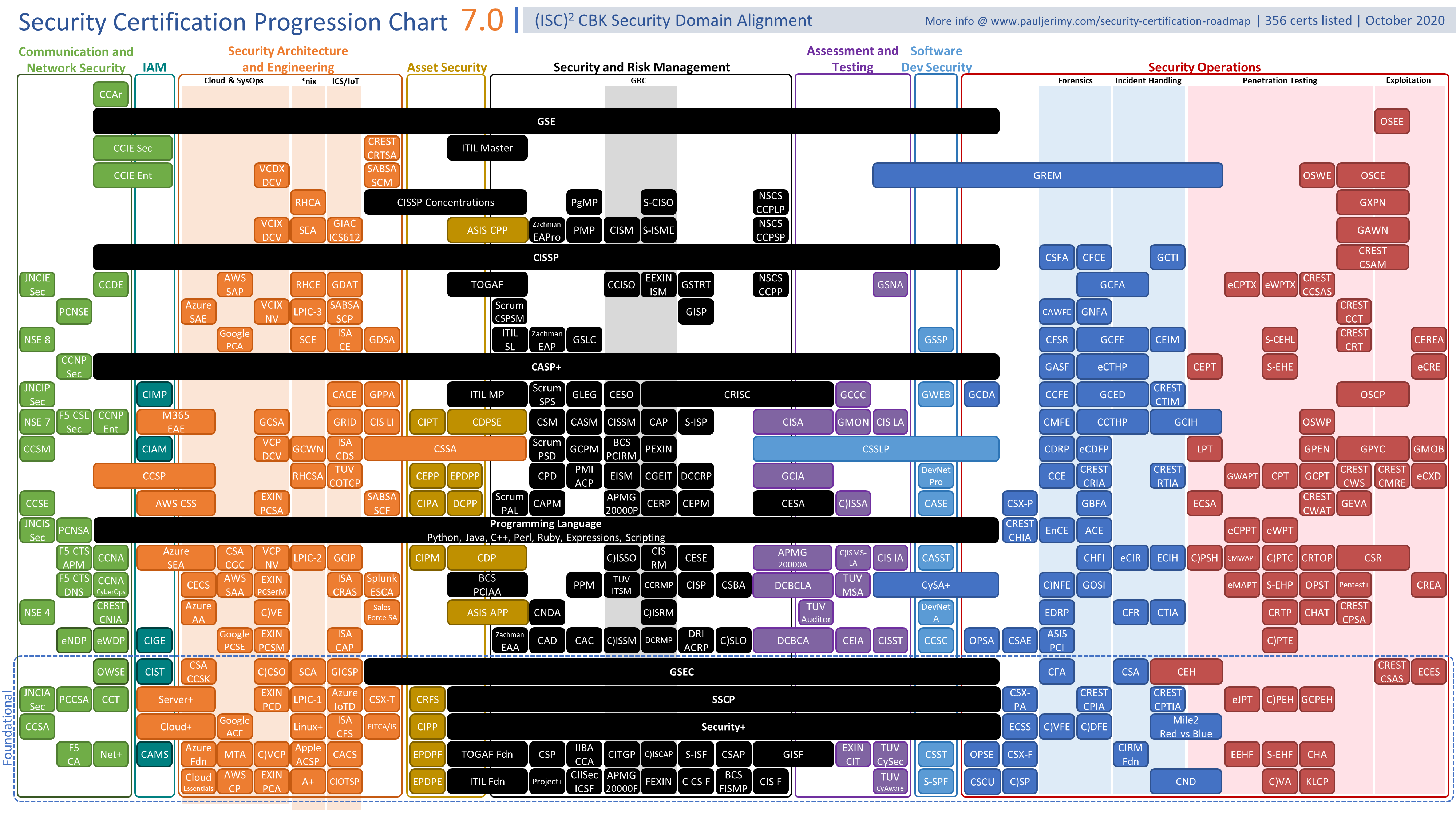
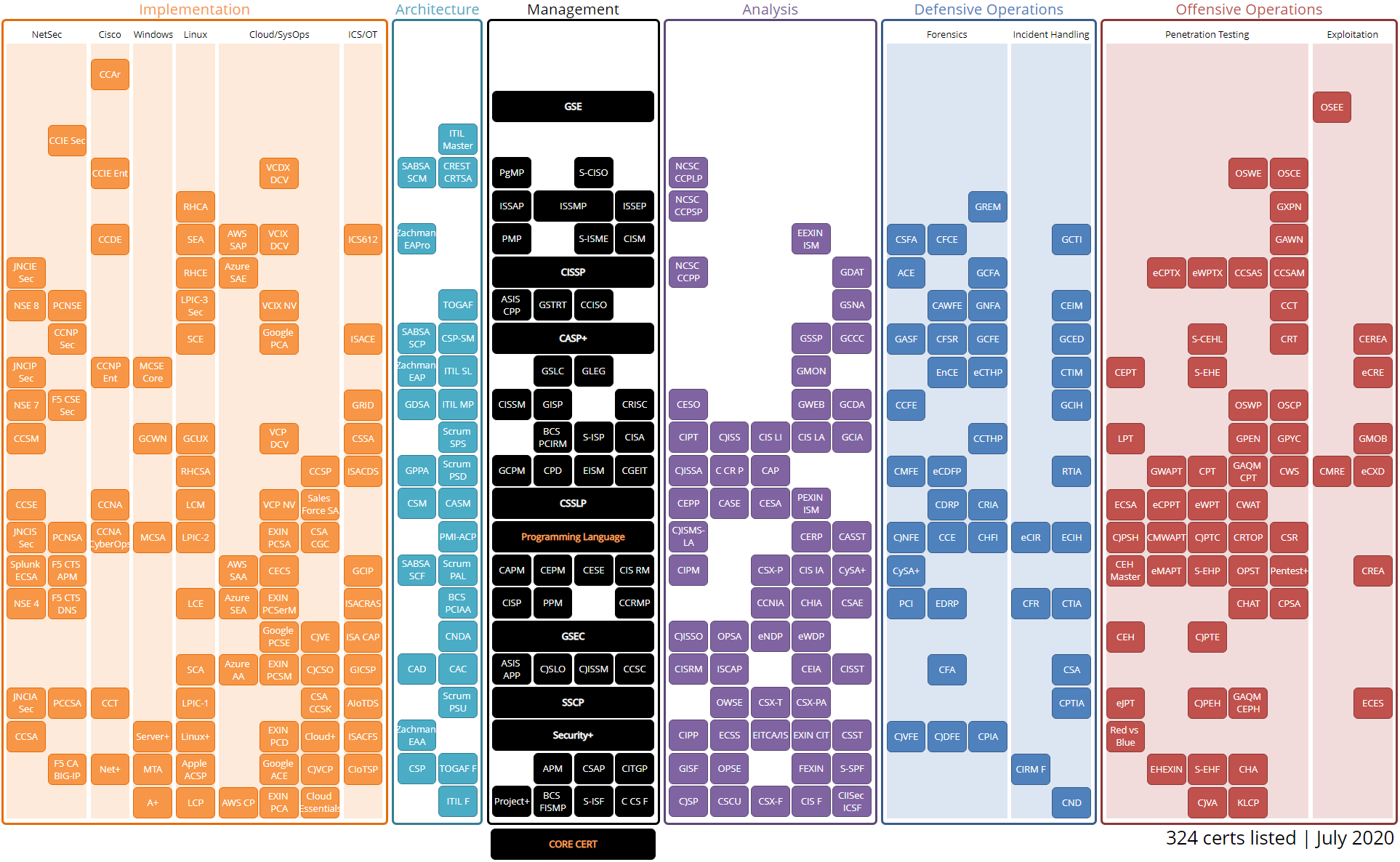
Dawn of the Code War: The U.S. was innocent, we swear!
My Reaction
This novel was a rough read but has some unique insights that make it worth finishing. I personally learned a lot about attacks conducted by the Chinese and Iranian nation states. I had heard of many, but some of the less public ones were interesting to hear about. Unfortunately there is very little in this novel about the technical mechanisms for those attacks. The descriptions are very focused on the politics and history of the events rather than the how.
The foreword and introduction were pointless, rambling, and exceedingly long. I recommend skipping those and starting with chapter 1. Things start to feel a bit more coherent and unique in chapter 2 where Carlin discusses events from the perspective of upper management in fledgling U.S. cyber programs. This perspective is refreshing as its not from the very detached top official and gives some insight into the formation of many U.S. organizations that have matured since his involvement.
Starting in the middle of chapter 4, Carlin’s bias towards the United States and the integrity of his organizations becomes clear and blatant and at odds with reality in some points. For instance, his argument for why Snowden was bad hinged on sunk costs and the fact that what he did was technically illegal. He was unapologetic about his role in spying on U.S. citizens and keeping the country’s cyber program hidden from the public. He posits that it was all legal and necessary because FISSA courts said its all fine.
Recommendation
I do not recommend this novel for security professionals. If you want a good history of cyber war from the U.S. perspective, I would pick up Dark Territory instead. There’s not much in Dawn of the Code War that’s worth exploring that’s not covered in there and Sandworm.

Suitable for:
IT Professionals
★★☆☆☆
Software Developers
★★☆☆☆
Security Analysts
★★☆☆☆
Security Engineers
★★☆☆☆
Security Operators
★★☆☆☆
CISO / CIOs
★★☆☆☆
Other Executives
★☆☆☆☆
My Rating
★★☆☆☆
Amazon Rating
★★★★⯪
Goodreads Rating
★★★★☆